OpenStack Summit: IoT, VNFs, and Security Services - How do they work together?
Internet of Things (IoT)
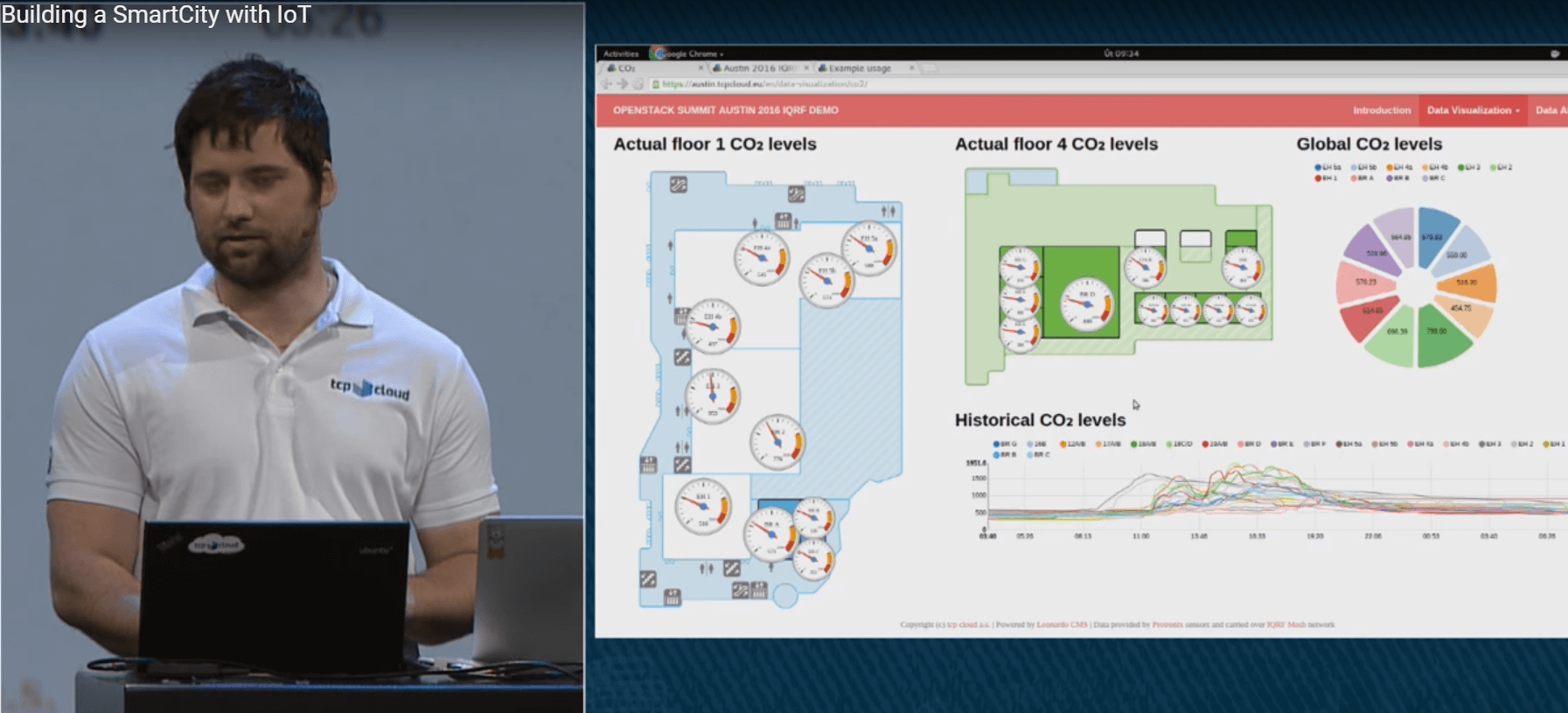
The IoT has come into our life, making our environment smarter. SmartCity, SmartHome, intelligent vehicles, and biosensors are far from a complete list of IoT applications.IoT is a compound statement that includes hardware devices and computing infrastructure to process, store, and analyze incoming data. Jakub Pavlík from tcpcloud showed a real life example of using IoT in his keynote “Building a SmartCity with IoT”, where he showed an IoT infrastructure example that had been deployed in the Austin Convention Center, consisting of twenty sensors to measure carbon dioxide level, temperature, and humidity in the summit premises. The data was then publicly available over the web during the course of the summit.
Juniper Networks foresees a rise from 13.4 billion devices in 2015 to 38 billion by 2020. A Cisco report contains even more impressive numbers - 50 billion IoT devices by 2020. All these devices will generate a huge amount of data to be processed, stored, and analyzed. One immediate thought is that the OpenStack platform can be used to handle incoming data, solving scalability, big data analysis, and security issues.
Security Threats and IoT
As we discussed during the panel discussion “OpenStack and the IoT,” security is a major concern in IoT infrastructure. The IoT attack surface includes two main components of IoT infrastructure:- the endpoint IoT devices such as sensors, cameras, IoT routers, and so on
- cloud computing, where the data from endpoint IoT devices is aggregated and analyzed
Cloud computing infrastructure is more attractive for an attacker than endpoint devices, as a cloud back end contains user-related information. Once attackers take over a cloud infrastructure, they can get access to users’ devices: webcams, door locks, cars, thermostats, and so forth. Some chipsets in IoT devices even contain hardcoded ssh keys to provide a manufacturer with access to troubleshoot devices. But what will happen if an attacker gets control over this information stored in the cloud?
VNFs and IoT
The IoT challenge for clouds is about processing of a fast growing amount of data coming from endpoint devices and providing the proper level of security at the same time, because failing to do so can lead to the compromise of millions of users’ IoT devices if attackers take over a communication channel or cloud infrastructure.Clouds must be elastic and provide the needed security level at any scale, and must be capable of analyzing incoming IoT data for the presence of anomalies that can indicate network traffic altering or spoofing by an attacker.
IoT data processing is usually done with service chaining that includes the following steps:
- aggregation
- verification
- transformation (if needed)
- analysis
- protection
To handle IoT data in a service chain in a fast and efficient way, NFVI provides a set of technologies to optimize CPU, memory, and network channel usage, including Data Plane Development Kit (DPDK), Single Root I/O Virtualization (SR-IOV), Non-Uniform Memory Access (NUMA), and Huge pages.
Security Services and IoT
VNFs provide a perfect way to process IoT data, enabling security services to function in a scalable and distributed manner. As an example, an open source security architecture based on VNFs was presented in the “Using Open Source Security Architecture to Defend against Targeted Attacks” session. This use case takes advantage of the OpenContrail SDN by Juniper, which can be easily deployed through a Fuel plugin, and shows how to enable a Network Intrusion Prevention System (IPS) as a VNF.IPS is a signature-based traffic scanner that capable of detecting known network attacks and extracting malicious files from network traffic. IPS is a basic way to protect your cloud against attack. You may also choose to install an antivirus, but this solution is not flexible as it requires antivirus client to be installed on every user’s VM, which leads to performance degradation within an environment.
To improve your protection level with IPS, you can buy a subscription for an extended set of IPS rules being regularly updated with Indicators-of-Compromise (IoC) for the latest threats such as IPs and domains used in an attack.
You can do even more, such as using a malware sandbox to run and analyze all files coming into the cloud from the Internet such as email attachments and direct downloads from an attacker’s server. Intrusion Protection Systems, for example, Snort and Suricata, can parse application level protocols (HTTP and SMTP) to extract suspicious files from the network stream. You can verify these files by requesting information in a whitelist and blacklist. If the file is unknown, you can forward it to a malware sandbox such as the open source Cuckoo Sandbox.






